Security Management
You are here:
- Home
- Security Management
Identity and Access Management (IAM)
Identity and Access Management solutions help an organization align its security management strategy with its business goals by automatically managing who has access to which resources and services; logging and reporting what they have done; and enforcing business, privacy and security policies Identity and Access Management solutions span Enterprise, customer and federated identities.
Security Information Management (SIM)
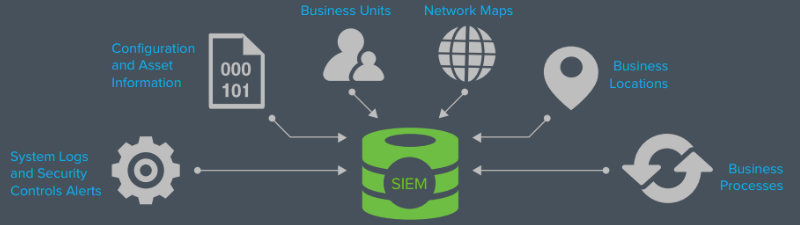
Security Information Management solutions help ensure that an organization is controlling its security infrastructure rather than being controlled by it. Centralized management of real-time events or post event forensics analysis helps improve administrator efficiencies and reduce costs, while integration and automation enhance effectiveness and security. In addition, these tools help ensure continuous business operations and provide the security views required to achieve regulatory compliance.
Threat Management
Threat Management solutions help prevent viruses, worms, spam and malicious content from infiltrating and infecting your network, email and business applications. They empower your security personnel to identify a threat to or weakness in your infrastructure, and help you take immediate actions preventing incidents before they negatively impact your assets. Threat Management solutions also confront content security challenges by keeping corporate content confidential and holding malicious content at bay.